Mar 01, 2024
Newsroom
Linux / Cyber Threat
Cybersecurity researchers have recently uncovered a new variant of the BIFROSE remote access trojan (RAT) specifically targeting Linux, using a deceptive domain that mimics VMware.
“This latest iteration of Bifrost is designed to evade security measures and compromise targeted systems,” mentioned Palo Alto Networks Unit 42 researchers Anmol Maurya and Siddharth Sharma in a statement.
Known as BIFROSE, this threat has been active since 2004 and has been a commodity in underground markets, fetching up to $10,000. Back in 2015, a report from Trend Micro highlighted this fact.
The malware has ties to a state-sponsored Chinese hacking group known as BlackTech, and has been deployed in cyber operations targeting entities in Japan, Taiwan, and the U.S.
Evidence suggests that the source code of Bifrost was obtained by the threat actors around 2010, leading to the development of custom backdoors like KIVARS and XBOW to support their operations.
Linux variants of BIFROSE, also known as ELF_BIFROSE, have been identified with abilities like launching remote shells, file downloads/uploads, and file manipulation since at least 2020.
The researchers explained, “Attackers typically distribute Bifrost via email attachments or malicious websites, allowing them to gather crucial details such as victim’s IP address and hostname.”
What sets this latest version apart is its connection to a command-and-control (C2) server named “download.vmfare[.]com,” posing as VMware. The domain deception is facilitated by a public DNS resolver in Taiwan with the IP address 168.95.1[.]1.
Unit 42 has observed a rise in Bifrost activity since October 2023, identifying over 100 artifacts in their telemetry, including an Arm version of the malware, hinting at an expansion of their target base.
Highlighting the risks posed by these new deceptive domain tactics, the researchers noted the surge in Bifrost activity as a cause for concern.
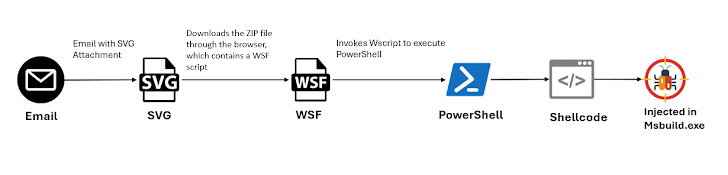
Concurrently, McAfee Labs unveiled a new GuLoader campaign that spreads through malicious SVG attachments in emails, expanding its reach via VBS scripts in a multi-stage payload delivery.
Trustwave SpiderLabs also emphasized the evolving tactics of these malware campaigns, such as the Bifrost and GuLoader attacks, pointing to a growing need for vigilance.
The surge in Bifrost and GuLoader attacks coincide with the announcement of a new version of the Warzone RAT, where two operators were recently arrested, leading to the dismantling of its infrastructure by authorities.