Feb 19, 2024
Newsroom
Malware / Cyber Espionage
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal.
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns targeting think tanks, NGOs, and journalists.
“CharmingCypress often employs unusual social-engineering tactics, such as engaging targets in prolonged conversations over email before sending links to malicious content,” Volexity researchers Ankur Saini, Callum Roxan, Charlie Gardner, and Damien Cash said.
Microsoft recently revealed that high-profile individuals working on Middle Eastern affairs have been targeted by the adversary to deploy malware capable of harvesting sensitive information from a compromised host.
The group, assessed to be affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has also distributed several other backdoors emphasizing its determination to continue its cyber onslaught, adapting its tactics and methods despite public exposure.
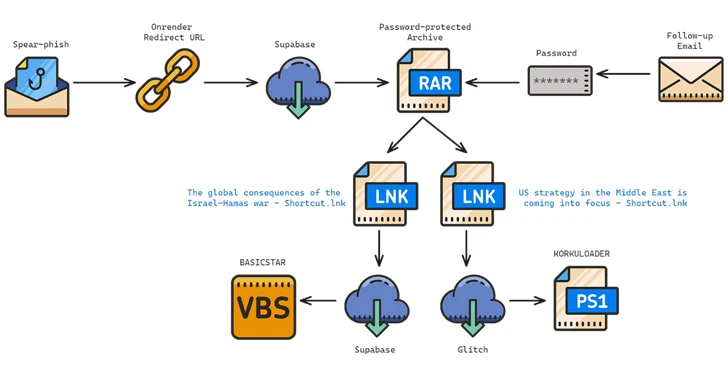
The phishing attacks observed between September and October 2023 involved the Charming Kitten operators posing as the Rasanah International Institute for Iranian Studies (IIIS) to initiate and build trust with targets.
The phishing attempts are also characterized by the use of compromised email accounts belonging to legitimate contacts and multiple threat-actor-controlled email accounts, the latter of which is called Multi-Persona Impersonation (MPI).
The attack chains typically employ RAR archives containing LNK files as a starting point to distribute malware.
BASICSTAR, a Visual Basic Script (VBS) malware, is capable of gathering basic system information, remotely executing commands, and downloading and displaying a decoy PDF file.